Random thoughts
Tuesday, September 29, 2009
Internet Summit Austria 2009
Today I attended the Internet Summit Austria 2009 held by the Internet Service Providers Austria association at the Austrian Academy of Sciences. The motto of the event was “We are Internet”, referring to the fact that the Internet is created by people and used by people.
ISPA chairman Andreas Koman opened the session with statistics about Internet use in Austria and an overview of current developments and challenges.
Claudia Bandion-Ortner, minister of justice, admitted her preference for paper files and reminded the audience that the Internet is not an area unregulated by law. There are legal issues specific to information technology, such as data theft and violation of data privacy rights. While fraudsters and other criminals use the Internet, most crimes are media neutral. One area that is closely linked to the Internet, though, is child pornography. Bandion-Ortner referred to the controversial German pilot for blocking access to illegal sites. Needless to say, the same filter technology could be used for censoring access to legitimate information or enforcing intellectual property rights.
Volker Grassmuck delivered a keynote about the reformation of intellectual property law in the digital age. Established “common sense” can block creativity and innovation. Some ideas worked well although most people would have assumed they wouldn’t:
On net neutrality Grassmuck mentioned a speech by FCC chairman Julius Genachowski and a refined view on the issue, with net neutrality but with network management to handle congestion or spam and with provisions for law enforcement, and transparency which would allow blocking or throttling certain types of traffic as long as customers are made aware.
There is no one solution that satisfies the needs of content producers, consumers and intermediaries. Working models will require a combination of an agreement between creative professionals and society, markets, free licenses, public subsidies and a “cultural flat rate”.
One of the conference gifts was, ironically, a USB stick with a locked down installation of Firefox using the Tor network to ensure privacy.
The keynote was followed by a lively discussion about intellectual property rights, including but not limited to compensation for the creator of content. The composer Johanna Doderer and the author Gerhard Ruiss pointed out that they want to maintain control over what happens with their works and reminded the audience that creative professionals are typically paid by how often their works sell. Georg Hitzenberger of Play.fm and Bettina Kann of the Austrian National Library outlined some of the challenges with obtaining rights for use in digital media and making content available. For example, the digital Web archive maintained by the Austrian National Library has unreasonably strict access requirements in selected locations only, one person at a time. Franz Schmidbauer touched on legal aspects and the adequacy of intellectual property rights enforcement.
MEP Eva Lichtenberger made an interesting comment about giving young people the ability to purchase digital media without requiring a credit card, quoting the large amounts spent on ringtones where suitable payment solutions are offered by telecom providers.
After the lunch break, Peter A. Gloor gave an entertaining presentation about “Coolhunting by Swarm Creativity” (that’s a lot of buzzwords for a title), explaining how their system combines different inputs–the wisdom of the crowd in the form of the Web, the wisdom of the swarms in the dynamics of fora and blogs, the knowledge in news and Wikipedia–to understand networks, trends and content. “Experts are right – in 50% of the cases. You never know which 50% you have.” swarmcreativity.net and ickn.org have good information about the concepts and the Condor software for non-commercial use.
Two panel discussions about social networks and business on the Internet concluded the agenda.
ISPA chairman Andreas Koman opened the session with statistics about Internet use in Austria and an overview of current developments and challenges.
Claudia Bandion-Ortner, minister of justice, admitted her preference for paper files and reminded the audience that the Internet is not an area unregulated by law. There are legal issues specific to information technology, such as data theft and violation of data privacy rights. While fraudsters and other criminals use the Internet, most crimes are media neutral. One area that is closely linked to the Internet, though, is child pornography. Bandion-Ortner referred to the controversial German pilot for blocking access to illegal sites. Needless to say, the same filter technology could be used for censoring access to legitimate information or enforcing intellectual property rights.
Volker Grassmuck delivered a keynote about the reformation of intellectual property law in the digital age. Established “common sense” can block creativity and innovation. Some ideas worked well although most people would have assumed they wouldn’t:
- Shared space pioneered by Hans Moderman–“If you treat people like idiots, they will behave like idiots.”
- Shared code with the Free Software Foundation (FSF)
- Shared profits with the micro-payments of the Grameen bank– “People behave in a trustworthy way when they are trusted.”
On net neutrality Grassmuck mentioned a speech by FCC chairman Julius Genachowski and a refined view on the issue, with net neutrality but with network management to handle congestion or spam and with provisions for law enforcement, and transparency which would allow blocking or throttling certain types of traffic as long as customers are made aware.
There is no one solution that satisfies the needs of content producers, consumers and intermediaries. Working models will require a combination of an agreement between creative professionals and society, markets, free licenses, public subsidies and a “cultural flat rate”.
One of the conference gifts was, ironically, a USB stick with a locked down installation of Firefox using the Tor network to ensure privacy.
The keynote was followed by a lively discussion about intellectual property rights, including but not limited to compensation for the creator of content. The composer Johanna Doderer and the author Gerhard Ruiss pointed out that they want to maintain control over what happens with their works and reminded the audience that creative professionals are typically paid by how often their works sell. Georg Hitzenberger of Play.fm and Bettina Kann of the Austrian National Library outlined some of the challenges with obtaining rights for use in digital media and making content available. For example, the digital Web archive maintained by the Austrian National Library has unreasonably strict access requirements in selected locations only, one person at a time. Franz Schmidbauer touched on legal aspects and the adequacy of intellectual property rights enforcement.
MEP Eva Lichtenberger made an interesting comment about giving young people the ability to purchase digital media without requiring a credit card, quoting the large amounts spent on ringtones where suitable payment solutions are offered by telecom providers.
After the lunch break, Peter A. Gloor gave an entertaining presentation about “Coolhunting by Swarm Creativity” (that’s a lot of buzzwords for a title), explaining how their system combines different inputs–the wisdom of the crowd in the form of the Web, the wisdom of the swarms in the dynamics of fora and blogs, the knowledge in news and Wikipedia–to understand networks, trends and content. “Experts are right – in 50% of the cases. You never know which 50% you have.” swarmcreativity.net and ickn.org have good information about the concepts and the Condor software for non-commercial use.
Two panel discussions about social networks and business on the Internet concluded the agenda.
Labels: austria, events, technology, web2.0
Friday, September 25, 2009
Brain food

The program started in early September with one week of lectures at the Burg Schlaining conference center. Besides getting an introduction into the concepts of law, registering and picking up the text books and DVDs, we had sufficient time for socializing and getting to know fellow students. On the first evening, the major invited to a reception at the town hall. I appreciated the warm welcome and thoroughly enjoyed the week, learning something new in the relaxed atmosphere of scenic Stadtschlaining and meeting nice people.
Having spent a good portion of my study period with checking bulletin boards distributed throughout the campus for announcements and organizing the study—the Web had not been invented—I was positively impressed how well things were organized here. The lectures and practice sessions are available on DVDs or as video streams, and textbooks are available for all courses, eliminating the need to take illegible notes.
What's nice about the program is the flexibility where and when you study. Of course that flexibility comes with the risk of procrastination, so feel free to ask me about my progress from time to time (read: no more than once a quarter!) as a gentle reminder.
Will I become a lawyer some day? Probably not. I haven't given much thought to how a law degree might change my career plans. Either way, it will be worth it to me.
Tuesday, August 11, 2009
Security, privacy, and an inconvenience
Redirects are often discussed only in the context of search engine optimization (SEO). Here is a good example how redirects affect users as well, and why it is important to choose your redirects wisely.
The Central Intelligence Agency (CIA) in 2006 began serving its Website encrypted in an effort to improve security and privacy of the communication.
This is a clear case for a 301 redirect from the unencrypted URL http://www.cia.gov/page to the equivalent encrypted URL https://www.cia.gov/page. Instead, except for the homepage and very few other pages, all requests get redirected to a splash page informing visitors about the site changes:
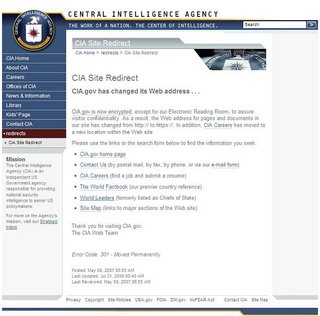
Not only is this a bad idea for search since all those links out there on various sites now transfer link weight to a splash page which is marked as non-indexable. It is also an inconvenience to users who need to navigate to the specific content or go back to the previous page and try again with an edited link.
Even the old URL for the World Factbook, arguably one of the most popular resources on the site, no longer goes to the desired World Factbook homepage directly.
The CIA press release states: “We believe the inconveniences of implementing SSL for the entire website will be offset by increased visitor confidence that they are, in fact, connected to the CIA website and that their visits are secure and confidential.”
The effort to increased security and privacy is commendable, and encrypting all communication with the agency certainly isn't a bad idea. Doing so without the inconveniences would be even better though, and perfectly feasible, too.
The Central Intelligence Agency (CIA) in 2006 began serving its Website encrypted in an effort to improve security and privacy of the communication.
This is a clear case for a 301 redirect from the unencrypted URL http://www.cia.gov/page to the equivalent encrypted URL https://www.cia.gov/page. Instead, except for the homepage and very few other pages, all requests get redirected to a splash page informing visitors about the site changes:

Not only is this a bad idea for search since all those links out there on various sites now transfer link weight to a splash page which is marked as non-indexable. It is also an inconvenience to users who need to navigate to the specific content or go back to the previous page and try again with an edited link.
Even the old URL for the World Factbook, arguably one of the most popular resources on the site, no longer goes to the desired World Factbook homepage directly.
The CIA press release states: “We believe the inconveniences of implementing SSL for the entire website will be offset by increased visitor confidence that they are, in fact, connected to the CIA website and that their visits are secure and confidential.”
The effort to increased security and privacy is commendable, and encrypting all communication with the agency certainly isn't a bad idea. Doing so without the inconveniences would be even better though, and perfectly feasible, too.
Labels: networking, seo, technology
Monday, August 10, 2009
SEO advice: Redirect wisely
More often than not you will see someone recommend switching all redirects on your site to 301s because they pass “link equity” in Google. There is the simple and neat solution for search engine optimization, and it could be plain wrong. At the risk of diverging from the consensus in your favorite discussion forum or offending your SEO consultant, read on and decide for yourself.
Redirects instruct browsers and search engine crawlers that content is available under a different URL. They often go unnoticed as we access Websites. Along with the new location of the content, the server also sends a response code indicating the type of redirect. From an SEO perspective, you generally care about two response codes, 301 Moved permanently and 302 Found:
Let's summarize the effects of the two most common redirect status codes again:
The 301 redirect response is appropriate for the following scenarios:
When Google introduced the “canonical” meta tag in February 2009, this suddenly made sense. Once multiple URLs are known to refer to the same page, or a slight variation of a page, the index only needs to keep one instance of the page.
The canonical meta tag helps the webmaster of a site who give search engines a hint about the preferred URL. The canonical meta tag also helps search engines since mapping multiple crawled URLs to the same page and indexing it only once just became easier.
Whether link equity fully transfers between multiple URLs mapped to the same page remains to be seen. At least within the same domain, this unification process may allow keeping the vanity URL in the index with a 302 redirect response while still transferring link equity.
PS. For an excellent and detailed description how redirects work, how to configure your Web server and what each status code does, see Sebstian's pamphlet The anatomy of a server sided redirect: 301, 302 and 307 illuminated SEO wise.
Redirects instruct browsers and search engine crawlers that content is available under a different URL. They often go unnoticed as we access Websites. Along with the new location of the content, the server also sends a response code indicating the type of redirect. From an SEO perspective, you generally care about two response codes, 301 Moved permanently and 302 Found:
- 301 Moved permanently indicates that the resource has been assigned a different URL permanently, and the original URL should no longer be used. What this means for Search engines is that should index the new URL only. Google also transfers full link equity with a 301 redirect, which is the very reason why you will often see the advice to use 301 redirects.
- 302 Found indicates that the originally requested URL is still valid, and should continue to be used. Search engines vary in how they treat 302 redirects and which URL they show in search result pages, but generally will continue to crawl the original URL as recommended in the HTTP/1.1 specification: “The requested resource resides temporarily under a different URI. Since the redirection might be altered on occasion, the client SHOULD continue to use the Request-URI for future requests.”
Choosing the right redirect response code
So which redirect response code should you use? Matt Cutts' description how Google treats on-domain and off-domain 302 redirects covers the basic principles and the heuristics that Google used at the time, which to a large extent still apply.Let's summarize the effects of the two most common redirect status codes again:
- 301 redirects transfer link equity to the new URL.
- 301 redirects remove the original URL from the search index.
- 302 redirects often keep the original URL in the index.
The 301 redirect response is appropriate for the following scenarios:
- Content has moved to a different location permanently, for example to a different server name or a different directory structure of the same server. This may be triggered by the rebranding of content where you want all references to the original content to disappear.
- A Website is accessible under multiple host names, such as example.com and www.example.com, or typo catchers like eggsample.com and example.org, but only one name should be indexed.
- A temporary campaign URL is published in direct mail or print advertising, but the landing page has a different permanent URL that will remain accessible beyond the lifetime of the campaign.
- The requested URL does not match the canonical URL for the resource. Often extraneous session and tracking parameters can be stripped, or path information gets added to help with search rankings, for example http://www.amazon.com/Software-
Development- Principles- Patterns- Practices/dp/0135974445
- The original URL is shorter, prettier, more meaningful, etc. and therefore should show on the search engine results page.
- Temporary session or tracking information gets added to the canonical URL. Those URL parameters should not be indexed since they will not apply to other visitors.
- Multiple load balanced servers deliver the content. Indexing an individual server would defeat the purpose of using load balancing. (There are better ways to load balance than having multiple server names, though.)
The “canonical” meta tag
How can you keep the short URL in the index and still transfer link equity? In summer 2008, we started observing that Google somehow “merged” related URLs and treated them as a single entity, showing identical page rank and identical number of inbound links to all of the URLs.When Google introduced the “canonical” meta tag in February 2009, this suddenly made sense. Once multiple URLs are known to refer to the same page, or a slight variation of a page, the index only needs to keep one instance of the page.
The canonical meta tag helps the webmaster of a site who give search engines a hint about the preferred URL. The canonical meta tag also helps search engines since mapping multiple crawled URLs to the same page and indexing it only once just became easier.
Whether link equity fully transfers between multiple URLs mapped to the same page remains to be seen. At least within the same domain, this unification process may allow keeping the vanity URL in the index with a 302 redirect response while still transferring link equity.
PS. For an excellent and detailed description how redirects work, how to configure your Web server and what each status code does, see Sebstian's pamphlet The anatomy of a server sided redirect: 301, 302 and 307 illuminated SEO wise.
Labels: networking, seo, webdevelopment
Tuesday, July 7, 2009
Wiener Neustadt is half way from Vienna to Jesolo
No, we didn't get the distances wrong. Granted, Wiener Neustadt is about 60 km from Vienna whereas the distance to Jesolo is 600 km.
We left home in the dusk on July 1 with our van fully loaded, expecting to reach our vacation destination Jesolo by noon. Shortly after we had passed Wiener Neustadt, we noticed strange sounds under the hood, and the engine temperature started to rise quickly. “Stop engine. Oil pressure low.” destroyed our hope to reach at least a service station.
 The towing service arrived promptly, we squeezed two child seats and ourselves into the tow truck and still hoped for a quick repair. The mechanic who first inspected our car suspected a more serious problem, and an hour later we had the sad certainty: our VW Sharan had suffered from a broken connecting rod and subsequent damage to the engine at less than 7000 km, “a manufacturing defect”. We would certainly not continue our journey with this car.
The towing service arrived promptly, we squeezed two child seats and ourselves into the tow truck and still hoped for a quick repair. The mechanic who first inspected our car suspected a more serious problem, and an hour later we had the sad certainty: our VW Sharan had suffered from a broken connecting rod and subsequent damage to the engine at less than 7000 km, “a manufacturing defect”. We would certainly not continue our journey with this car.
We weren't ready to give up, though. After all we had made travel arrangements, and the kids were excited about our first vacation trip abroad. Volkswagen offers a Mobility Guarantee, which sounds like you would retain your mobility when your car breaks down. It includes free roadside assistance and towing, which was indeed helpful, and a replacement vehicle of Volkswagen's choice for three days. Subject to availability, that is. Three days wouldn't helped much anyway but the rental car partner mentioned they had no large vans available for the rest of the year (mind you, this was on July 1!) and actually had no cars available at all, not even for an hour to drive to the airport to pick up another car. As good as the mobility guarantee sounds, it was pretty useless when we needed it.
It's summer time and most car rental companies were short on cars. In the end we managed to arrange for a reasonable large Opel Zaphira with the help of a wonderful agent at weekrent.com and I took the train back to Vienna to get the car. Meanwhile Andrea stayed at the dealership with two tired kids, not a good way to start a holiday.
We left Wiener Neustadt in the afternoon and arrived in Jesolo late at night, tired but glad that we made it after all.
We left home in the dusk on July 1 with our van fully loaded, expecting to reach our vacation destination Jesolo by noon. Shortly after we had passed Wiener Neustadt, we noticed strange sounds under the hood, and the engine temperature started to rise quickly. “Stop engine. Oil pressure low.” destroyed our hope to reach at least a service station.
 The towing service arrived promptly, we squeezed two child seats and ourselves into the tow truck and still hoped for a quick repair. The mechanic who first inspected our car suspected a more serious problem, and an hour later we had the sad certainty: our VW Sharan had suffered from a broken connecting rod and subsequent damage to the engine at less than 7000 km, “a manufacturing defect”. We would certainly not continue our journey with this car.
The towing service arrived promptly, we squeezed two child seats and ourselves into the tow truck and still hoped for a quick repair. The mechanic who first inspected our car suspected a more serious problem, and an hour later we had the sad certainty: our VW Sharan had suffered from a broken connecting rod and subsequent damage to the engine at less than 7000 km, “a manufacturing defect”. We would certainly not continue our journey with this car.We weren't ready to give up, though. After all we had made travel arrangements, and the kids were excited about our first vacation trip abroad. Volkswagen offers a Mobility Guarantee, which sounds like you would retain your mobility when your car breaks down. It includes free roadside assistance and towing, which was indeed helpful, and a replacement vehicle of Volkswagen's choice for three days. Subject to availability, that is. Three days wouldn't helped much anyway but the rental car partner mentioned they had no large vans available for the rest of the year (mind you, this was on July 1!) and actually had no cars available at all, not even for an hour to drive to the airport to pick up another car. As good as the mobility guarantee sounds, it was pretty useless when we needed it.
It's summer time and most car rental companies were short on cars. In the end we managed to arrange for a reasonable large Opel Zaphira with the help of a wonderful agent at weekrent.com and I took the train back to Vienna to get the car. Meanwhile Andrea stayed at the dealership with two tired kids, not a good way to start a holiday.
We left Wiener Neustadt in the afternoon and arrived in Jesolo late at night, tired but glad that we made it after all.
Monday, June 29, 2009
The return of the curvy cucumber
For two decades, the European Union carefully regulated the size and shape of fruit. Often this has been quoted, and rightly so, as an example of the over-regulation by the commission.

Announced in November 2008, the return of the curvy cucumber will become effective on July 1, 2009. Now all those cucumbers and carrots will be “allowed” to grow in all shapes and sizes again (not that they cared too much about EC directives anyway).
Standards usually make life convenient. Just imagine what driving a rental car would be like if manufacturers implemented their own concept of speed and steering controls (too bad that other controls like air condition and radio aren't standardized and often not self-explanatory). Or withdrawing money from the bank without standardized bank cards and ATMs. Or connecting to networks if they weren't all using the same protocols.
Regulating the size and shape of fruit and vegetables, on the other hand, doesn't make life more convenient unless you like to see the cucumbers lined up nicely in the fridge. To me, this is mostly an indication of an unhealthy desire to control everything, including Mother Nature. More than two decades ago, the movement which eventually became the Green party started questioning large technology projects, be it nuclear power plants or ecologically questionable hydropower plants. Many of the environmental and energy related issues still need to be addressed. But, at least we have the curvy cucumber back.

Announced in November 2008, the return of the curvy cucumber will become effective on July 1, 2009. Now all those cucumbers and carrots will be “allowed” to grow in all shapes and sizes again (not that they cared too much about EC directives anyway).
Standards usually make life convenient. Just imagine what driving a rental car would be like if manufacturers implemented their own concept of speed and steering controls (too bad that other controls like air condition and radio aren't standardized and often not self-explanatory). Or withdrawing money from the bank without standardized bank cards and ATMs. Or connecting to networks if they weren't all using the same protocols.
Regulating the size and shape of fruit and vegetables, on the other hand, doesn't make life more convenient unless you like to see the cucumbers lined up nicely in the fridge. To me, this is mostly an indication of an unhealthy desire to control everything, including Mother Nature. More than two decades ago, the movement which eventually became the Green party started questioning large technology projects, be it nuclear power plants or ecologically questionable hydropower plants. Many of the environmental and energy related issues still need to be addressed. But, at least we have the curvy cucumber back.
Labels: business, technology
Wednesday, June 24, 2009
Absentee voting and security
The disputed presidential elections in Iran reminded me of an observation a few weeks ago when the European Union held elections for the European Parliament.
Absentee voting, and mail voting in particular, present some interesting security and privacy challenges. For the European election, voters who wanted to cast their vote outside of their electoral district could request absentee ballots to vote in other districts or by mail. In a commendable effort to make voting as convenient as possible, the administration only required name, address and passport number for requesting absentee ballots and delivered them to voters by regular mail, leaving ample room for misuse already.
But I was unpleasantly surprised when I found a sticker(!) on my mailbox indicating that “important electoral mail” had been delivered:

Well intended for sure, but in my opinion the service orientation really went overboard here. With all the trust in the administration, the electoral process and the people in our neighborhood, privacy and security concerns should be considered.
Absentee voting, and mail voting in particular, present some interesting security and privacy challenges. For the European election, voters who wanted to cast their vote outside of their electoral district could request absentee ballots to vote in other districts or by mail. In a commendable effort to make voting as convenient as possible, the administration only required name, address and passport number for requesting absentee ballots and delivered them to voters by regular mail, leaving ample room for misuse already.
But I was unpleasantly surprised when I found a sticker(!) on my mailbox indicating that “important electoral mail” had been delivered:

Well intended for sure, but in my opinion the service orientation really went overboard here. With all the trust in the administration, the electoral process and the people in our neighborhood, privacy and security concerns should be considered.
Disagreeing with Jakob Nielsen on security—Password masking makes logins more secure
When it comes to usability, disagreeing with Jakob Nielsen is usually not an option. After all, he has been called king, czar, guru or Web usability for a reason, and his Alertbox offers invaluable advise most of the time.
Disagreeing with Jakob Nielsen on security is easier, especially when he advocates to remove password masking as a means to improve usability and claims that this doesn't lower security.
While not offering a high degree of protection, the password masking does a pretty good job for most situations. Certainly, a determined and skilled criminal would be able to observe which keys are pressed, or use other attack vectors to intercept my Web interactions. I am often surrounded by trustworthy people who still shouldn't know my passwords, don't care about my passwords and even politely turn their eyes away while I am logging in. Whether showing someone a Website or doing a demo to a larger audience, accessing protected areas of a site in a semi-public environment like a desk-sharing area at work or logging in from a mobile device, those little stars or dots protect my passwords well from becoming exposed.
Security and usability should not be conflicting objectives; in fact usability is an important aspect for any security system, or users will work around usability issues and use it in unintended ways, like copying and pasting passwords from a text file as Nielsen mentions. An extra checkbox to enable password masking just adds complexity to the user interface and may confuse users more than not being able to see their password.
Typing passwords on mobile devices (or foreign keyboards, for that matter) can be challenging. Some smartphones like the iPhone or the Nokia N95 show the letter as typed but then quickly replacing it with an asterisk, which is a reasonable compromise.
Instead of cluttering Web forms with additional checkboxes, web developers should demand that browsers and mobile devices provide an option to remove password masking when desired by the user. This would maintain the current level of security by not exposing the passwords to people looking over users' shoulders and address the usability issue for those who have difficulty typing their password and would benefit from visual feedback.
Until then, use this JavaScript bookmarklet to unmask password fields as needed:
(all on one line, or simply drag the Unmask passwords bookmarklet link to your bookmarks).
PS. More ways to reveal passwords in a controlled manner can be found in Martin Brinkmann's blog post Reveal your saved Passwords in Firefox.
Disagreeing with Jakob Nielsen on security is easier, especially when he advocates to remove password masking as a means to improve usability and claims that this doesn't lower security.
While not offering a high degree of protection, the password masking does a pretty good job for most situations. Certainly, a determined and skilled criminal would be able to observe which keys are pressed, or use other attack vectors to intercept my Web interactions. I am often surrounded by trustworthy people who still shouldn't know my passwords, don't care about my passwords and even politely turn their eyes away while I am logging in. Whether showing someone a Website or doing a demo to a larger audience, accessing protected areas of a site in a semi-public environment like a desk-sharing area at work or logging in from a mobile device, those little stars or dots protect my passwords well from becoming exposed.
Security and usability should not be conflicting objectives; in fact usability is an important aspect for any security system, or users will work around usability issues and use it in unintended ways, like copying and pasting passwords from a text file as Nielsen mentions. An extra checkbox to enable password masking just adds complexity to the user interface and may confuse users more than not being able to see their password.
Typing passwords on mobile devices (or foreign keyboards, for that matter) can be challenging. Some smartphones like the iPhone or the Nokia N95 show the letter as typed but then quickly replacing it with an asterisk, which is a reasonable compromise.
Instead of cluttering Web forms with additional checkboxes, web developers should demand that browsers and mobile devices provide an option to remove password masking when desired by the user. This would maintain the current level of security by not exposing the passwords to people looking over users' shoulders and address the usability issue for those who have difficulty typing their password and would benefit from visual feedback.
Until then, use this JavaScript bookmarklet to unmask password fields as needed:
for(var i=0;(var a=document.getElementsByTagName("input")[i]);i++){
if(a.getAttribute("type").indexOf("password")!=-1){
a.type="text"
}
}
window.focus();
(all on one line, or simply drag the Unmask passwords bookmarklet link to your bookmarks).
PS. More ways to reveal passwords in a controlled manner can be found in Martin Brinkmann's blog post Reveal your saved Passwords in Firefox.
Labels: technology, usability, webdevelopment
Friday, June 5, 2009
World Environmental Day 2009
Just in time for the World Environmental Day 2009, this morning a colleague shared an amazing animation showing air traffic over a 24 hour period:
Every yellow dot represents a flight with at least 250 passengers.
The animation was developed by the ZHAW Zürcher Hochschule für Angewandte Wissenschaften in cooperation with the Swiss science center Technorama (Larger version of the Air Traffic Worldwide video from ZHAW).
Watching this it becomes clear how even smallest improvements in fuel efficiency, reduction of emissions and optimization of flight patterns reduce the environmental impact (not that flying or most other forms of transportation will ever become eco-friendly). Smart traffic and transportation is also a theme in IBM's Smarter planet initiative.
So what did I do on World Environmental Day 2009? Nothing special, I used public transport as I do whenever possible, looked for local, organically grown food when doing my grocery shopping at the Naschmarkt (although a recent study suggests that shipping fruits and vegetables from warmer countries like Spain may be better environmentally than growing them in greenhouses locally, so much for trying to do the right thing), separated my waste—and calculated my ecological footprint at ecologicalfootprint.com and myfootprint.org, a great reminder how many of us use an above average share of natural resources.
Every yellow dot represents a flight with at least 250 passengers.
The animation was developed by the ZHAW Zürcher Hochschule für Angewandte Wissenschaften in cooperation with the Swiss science center Technorama (Larger version of the Air Traffic Worldwide video from ZHAW).
Watching this it becomes clear how even smallest improvements in fuel efficiency, reduction of emissions and optimization of flight patterns reduce the environmental impact (not that flying or most other forms of transportation will ever become eco-friendly). Smart traffic and transportation is also a theme in IBM's Smarter planet initiative.
So what did I do on World Environmental Day 2009? Nothing special, I used public transport as I do whenever possible, looked for local, organically grown food when doing my grocery shopping at the Naschmarkt (although a recent study suggests that shipping fruits and vegetables from warmer countries like Spain may be better environmentally than growing them in greenhouses locally, so much for trying to do the right thing), separated my waste—and calculated my ecological footprint at ecologicalfootprint.com and myfootprint.org, a great reminder how many of us use an above average share of natural resources.
Labels: travel
Saturday, May 30, 2009
IE6 DOM weirdness: It was the base and not the comma
I recently hacked a few lines of JavaScript for an online survey. The script looked fairly straightforward and worked well on Firefox in no time.
Fortunately I had just received a new ThinkPad (more about that later) and hadn't upgraded Internet Explorer yet. Testing with IE6, my code failed miserably. Debugging with the indispensable FireBug light tool revealed that a shared library function for accessing meta information didn't return any information. The very same library function was working nicely on the production Web site, though; at least we hadn't heard any complaints, which given the percentage of users accessing our Web site with IE6 was highly unlikely.
Staring at the screen in disbelieve, our resident jQuery guru eventually found the culprit. Unlike with the infamous Undefined is null or not an object problem, it was not an issue with an extra comma this time.
Rather, IE6 seems to get the structure of documents containing a
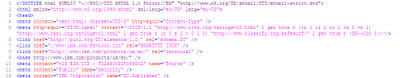
into this DOM tree:
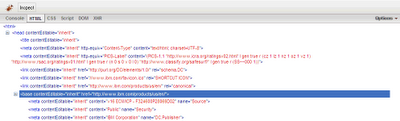
So the selector which was correctly looking for
Related information:
Fortunately I had just received a new ThinkPad (more about that later) and hadn't upgraded Internet Explorer yet. Testing with IE6, my code failed miserably. Debugging with the indispensable FireBug light tool revealed that a shared library function for accessing meta information didn't return any information. The very same library function was working nicely on the production Web site, though; at least we hadn't heard any complaints, which given the percentage of users accessing our Web site with IE6 was highly unlikely.
Staring at the screen in disbelieve, our resident jQuery guru eventually found the culprit. Unlike with the infamous Undefined is null or not an object problem, it was not an issue with an extra comma this time.
Rather, IE6 seems to get the structure of documents containing a
base tag wrong, making subsequent meta and link elements children of the base element, turning this source
into this DOM tree:

So the selector which was correctly looking for
html > meta would fail in the rare presence of a base tag, such as on a test page created by yours truly. The quick fix was a slightly less efficient selector html meta, and we were once again painfully reminded that IE6 tends to behave differently from current browsers and requires separate testing.Related information:
- Justin Rogers, BASE tag changes in IE 7 with Examples
Labels: javascript, webdevelopment, windows
Monday, April 6, 2009
301 Moved permanently
We are pleased to announce that we finally moved. Our new address: Buchbindergasse 6, A-1130 Wien.
The move went well and almost according to schedule.
We started packing on Tuesday, slowly filling a corner of my apartment with moving boxes. Christian had volunteered to help on Thursday, so we spent most of the day hauling some 30 boxes down three floors from the apartment, stuffing them into the van, driving to the house and unpacking stuff there so we could later reuse the boxes.





After three tours back and forth, wir hatten fertig.
Friday night was the time for the next round of packing boxes, and again we filled the storage space quickly. Amongst the packed stuff were some treasures that had long been lost, including two small booklets which were hidden under a pile of photographs, and a set of wedding pictures which mysteriously showed up behind a teapot!
Saturday was really the big moving day, with more boxes as well as furniture and other heavy stuff. Fortunately we had even more helping hands, and with a convoy of a rental transporter and two additional cars managed to move “everything” in just three more tours.








A big thank you to Christian, Michael and Rainer; you guys were absolutely terrific, and we would have never managed to move in two days without your great help.
We will spend the next few weeks organizing the new home and moving the remaining, less needed stuff that we left in the apartments. The house is currently filled with boxes waiting to be unpacked and things look slightly messy. Nevertheless we enjoyed the first night in our new home, and Elias tiptoeing over to our bedroom and giving us a gentle wakeup the next morning.
Lastly, we had our DSL line installed today; now if only I could find all the cables in one of the boxes…



The move went well and almost according to schedule.
We started packing on Tuesday, slowly filling a corner of my apartment with moving boxes. Christian had volunteered to help on Thursday, so we spent most of the day hauling some 30 boxes down three floors from the apartment, stuffing them into the van, driving to the house and unpacking stuff there so we could later reuse the boxes.





After three tours back and forth, wir hatten fertig.
Friday night was the time for the next round of packing boxes, and again we filled the storage space quickly. Amongst the packed stuff were some treasures that had long been lost, including two small booklets which were hidden under a pile of photographs, and a set of wedding pictures which mysteriously showed up behind a teapot!
Saturday was really the big moving day, with more boxes as well as furniture and other heavy stuff. Fortunately we had even more helping hands, and with a convoy of a rental transporter and two additional cars managed to move “everything” in just three more tours.








A big thank you to Christian, Michael and Rainer; you guys were absolutely terrific, and we would have never managed to move in two days without your great help.
We will spend the next few weeks organizing the new home and moving the remaining, less needed stuff that we left in the apartments. The house is currently filled with boxes waiting to be unpacked and things look slightly messy. Nevertheless we enjoyed the first night in our new home, and Elias tiptoeing over to our bedroom and giving us a gentle wakeup the next morning.
Lastly, we had our DSL line installed today; now if only I could find all the cables in one of the boxes…



Sunday, March 22, 2009
rsync does work with plink
For years rsync from the cygwin distribution and PuTTY's plink program would not work together and fail with
Unable to read from standard input: The handle is invalid.
rsync: read error: Connection reset by peer (104)
I first posted this problem to comp.security.ssh in 2005 but never received a solution, until now.
Frank Behrens published cygnative, a small wrapper program that resolves an incompatibility between cygwin and Win32 native programs. With cygnative, invoking rsync with plink as the remote shell works like a charm:
rsync -ave "cygnative plink -batch" source target
Thank you, Frank!
Unable to read from standard input: The handle is invalid.
rsync: read error: Connection reset by peer (104)
I first posted this problem to comp.security.ssh in 2005 but never received a solution, until now.
Frank Behrens published cygnative, a small wrapper program that resolves an incompatibility between cygwin and Win32 native programs. With cygnative, invoking rsync with plink as the remote shell works like a charm:
rsync -ave "cygnative plink -batch" source target
Thank you, Frank!
Labels: networking, windows
Thursday, March 19, 2009
We are moving
We have finally settled on the moving dates to our new home: April 2 and 4. We plan to move a good portion of the boxes by car on the first day, and get a transporter to move the larger furniture, the remaining boxes, and other stuff on the second day. That leaves one day in between to recover from hauling boxes and furniture down three floors from our apartments, and then up one or two floors in the house.
Help needed!
We greatly appreciate any help you can give us with the move, including packing and unpacking, disassembling and reassembling furniture, moving stuff around, and last but not least looking after the kids (that is, feeding Daniel during the day as needed and keeping an eye on Elias when he returns from kindergarten, or taking him to the nearby playground, weather permitting). Hints and tools for moving are also welcome.
Please kindly let us know if you can help us with the move. Food and drinks will be provided at the house.
(Last updated March 31, 2009)
Help needed!
We greatly appreciate any help you can give us with the move, including packing and unpacking, disassembling and reassembling furniture, moving stuff around, and last but not least looking after the kids (that is, feeding Daniel during the day as needed and keeping an eye on Elias when he returns from kindergarten, or taking him to the nearby playground, weather permitting). Hints and tools for moving are also welcome.
Please kindly let us know if you can help us with the move. Food and drinks will be provided at the house.
(Last updated March 31, 2009)
Monday, February 23, 2009
Amazon.com: User experience delivering value
While shopping on Amazon the other day, I noticed a subtle yet still noticeable hint that I had bought the very same article already in October 2007.
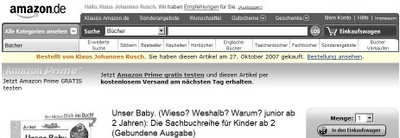
At first glance, the notice would appear to drive customers away from buying; however Amazon.com has a long-standing reputation for innovation in online commerce and good customer service (although I have been less satisfied with their handling of e-mail correspondence lately) so this didn't come as a complete surprise.
Good user experience design is all about delivering value to the customer, and to the business too:
Links:

At first glance, the notice would appear to drive customers away from buying; however Amazon.com has a long-standing reputation for innovation in online commerce and good customer service (although I have been less satisfied with their handling of e-mail correspondence lately) so this didn't come as a complete surprise.
Good user experience design is all about delivering value to the customer, and to the business too:
- The customer may have bought the product earlier and order another copy as a present, which was actually the case for me.
- Some products, such as blank CDs/DVDs, lend themselves to repetitive orders. Knowing that this is the same product ordered before is reassuring to the customer, which means more business with fewer clicks.
- In the unlikely case that a customer accidentally orders the same product twice, chances are that she would return the product for a refund, incurring shipping and handling cost for the business; therefore not shipping the product in the first place is not only the most customer friendly, but also the most cost effective solution.
Links:
Labels: business, ibm, kudos, technology
Apple juice and milk
After cleaning my office chair from milk, the results of Daniel's inverse peristalsis, I wasn't planning to clean the keyboard next. That was before I poured a glass of naturally cloudy apple juice over it. From a quick glance the keyboard looks alright; the keys popped out quite easily, albeit with a crackling sound, and the electronics stayed dray, or so I hope.
I will remind myself that food and typing don't go well together and enjoy the comfort of a clean keyboard for a while before falling back to my bad habits :-)
PS. Speaking of milk, on Saturday night we went to the cinema to see Gus Van Sant's beautiful and highly acclaimed movie Milk on the life of gay rights activist and politician Harvey Milk, portrayed by Sean Penn, who just received an academy award for his performance this weekend.
I will remind myself that food and typing don't go well together and enjoy the comfort of a clean keyboard for a while before falling back to my bad habits :-)
PS. Speaking of milk, on Saturday night we went to the cinema to see Gus Van Sant's beautiful and highly acclaimed movie Milk on the life of gay rights activist and politician Harvey Milk, portrayed by Sean Penn, who just received an academy award for his performance this weekend.
Saturday, January 31, 2009
Google: This site may harm your computer
Google generally does a pretty good job warning users about suspicious Web sites assumed to contain malware, but their algorithm seems to have gone overboard now. This morning every search result shows a warning that the site may harm my computer:
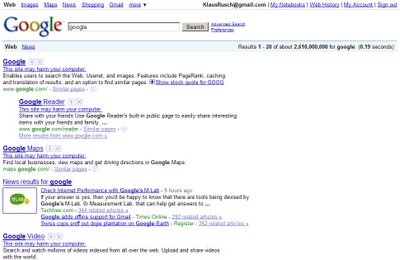

Labels: google, technology
Wednesday, January 14, 2009
Summer inside, winter outside

We had this winter's first snow today in Vienna (not counting the few snowflakes back in December). Fortunately temperatures are up again after a rather chilly week, and that was not just because Russian gas stopped reaching Europe.
Labels: personal
Thursday, January 1, 2009
Happy New Year 2009

Wish you Happy and Prosperous New Year 2009!
We returned to Vienna tonight from our family tour to Salzburg, Munich, Dornbirn and Salzburg again.
It was good to see our families again, including the first meeting of little Daniel with his great grandmothers. At the same time it feels like we spent most the last 10 days driving (or, getting stuck in traffic jams), so we are glad to be home.
Wednesday, December 31, 2008
0101001011101010111
Google search nicely reminded me that digital storage is still all about ones and zeros:
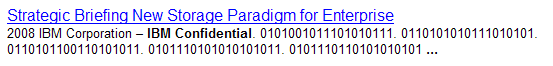

Labels: ibm, technology
Wednesday, December 24, 2008
Season's Greetings 2008

Festivus, Kwanza, Christmas, Hanukkah, Solstice, whatever you celebrate at this time of year: Happy holidays and all the best for the new year!
PS. Daniel wasn't unhappy at all with the hat, except of course when we shot the picture.
Labels: personal
